LABORATORY MONTORING system
technology innovation for modern laboratories

CCTV AI (Artificial Intelligence) adalah kamera pengawas dengan teknologi kecerdasan buatan yang mampu menganalisis video secara real-time untuk memberikan informasi lebih cerdas daripada CCTV biasa.
Di bidang kesehatan, CCTV AI digunakan untuk memantau pasien, mendeteksi insiden seperti pasien jatuh, memonitor kerumunan, memastikan kepatuhan protokol kesehatan, serta meningkatkan keamanan dan efisiensi operasional rumah sakit.

Dalam era digitalisasi layanan kesehatan, PT Alizah berkomitmen menghadirkan layanan dan perangkat medis yang aman, andal, dan berkelanjutan dengan mengintegrasikan keamanan siber di setiap tahapan pengembangan produk, membangun budaya perlindungan data di seluruh lini perusahaan, serta menjalin kolaborasi dengan tenaga kesehatan, regulator, dan pemangku kepentingan lainnya guna menciptakan ekosistem kesehatan yang tangguh terhadap ancaman digital.

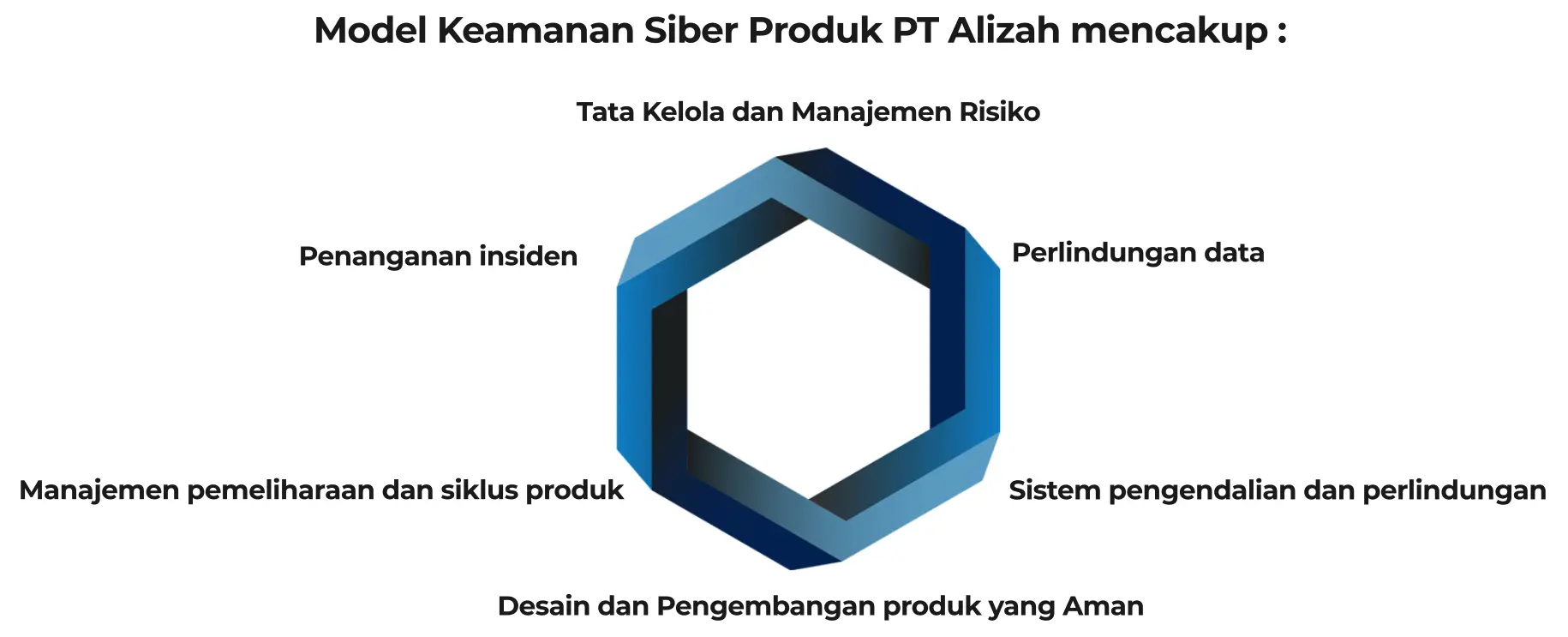
- Tata Kelola dan Manajemen Risiko
- Perlindungan data
- Sistem pengendalian dan perlindungan
- Desain dan Pengembangan produk yang Aman
- Manajemen pemeliharaan dan siklus produk
- Penanganan insiden
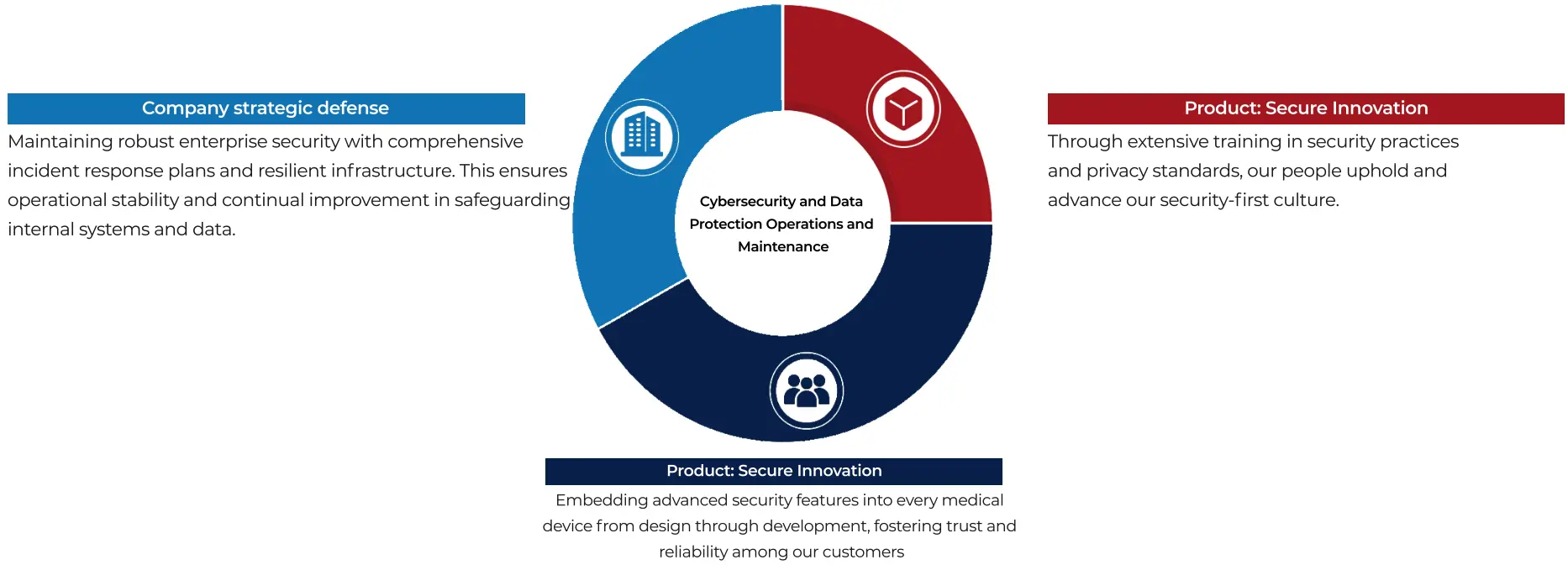
Company strategic defense
Maintaining robust enterprise security with comprehensive incident response plans and resilient infrastructure. This ensures operational stability and continual improvement in safeguarding internal systems and data
Product: Secure Innovation
Through extensive training in security practices and privacy standards, our people uphold and advance our security-first culture.
Product: Secure Innovation
Embedding advanced security features into every medical device design through development, fostering trust and reliability among our customers.
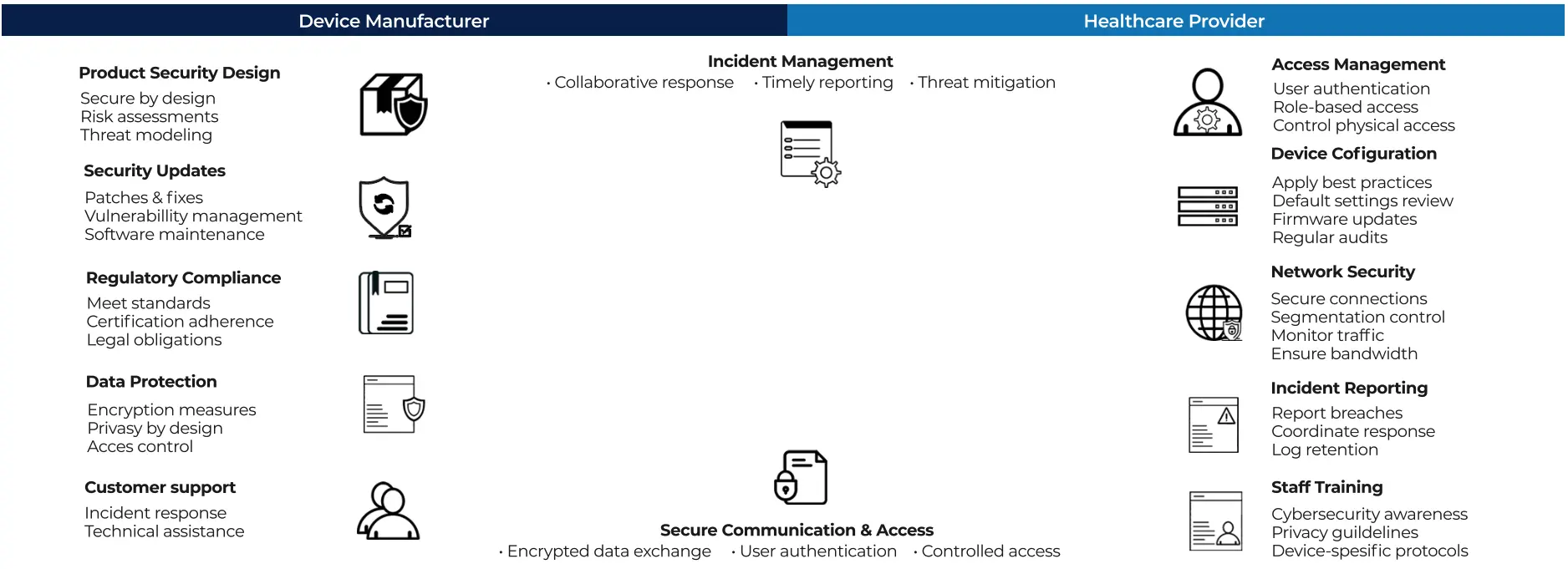
Device Manufacturer
Product Security Design
Secure by design
Risk assessments
Threat modeling

Security Updates
Patches & fixes
Vulnerability management
Software maintenance
Regulatory Compliance
Meet standards
Certification adherence
Legal obligations
Data Protection
Encryption measures
Privacy by design
Access control
Customer support
Incident response
Technical assistance
Incident Management
Collaborative response
Timely reporting
Threat mitigation
Secure Communciation & Access
Encrypted data exchange
User authentication
Controlled access
Healthcare Provider
Access Management
User authentication
Role-based access
Control physical access

Device Configuration
Apply best practices
Default settings review
Firmware updates
Regular audits
Network Security
Secure connections
Segmentation control
Monitor traffic
Ensure bandwith

Incident Reporting
Report breaches
Coordinate response
Log retention

Staff Training
Cybersecurity awareness
Privacy guidelines
Device-spesific protocols
Incident Management
Collaborative response
Timely reporting
Threat mitigation

Secure Communciation & Access
Encrypted data exchange
User authentication
Controlled access